<dependency>
<groupId>io.micronaut.azure</groupId>
<artifactId>micronaut-azure-secret-manager</artifactId>
<scope>compile</scope>
</dependency>Table of Contents
- 1. Getting Started
- 2. What you will need
- 3. Creating the Application
- 4. Micronaut Azure Key Vault Dependencies
- 5. Update the Application configuration to use Azure Key Vault secrets
- 6. Store JDBC secrets in Azure Key Vault using Azure Portal
- 7. Running the Application
- 8. Cleaning Up
- 9. Next Steps
- 10. Help with the Micronaut Framework
- 11. License
Securely store Micronaut Application secrets in Azure Key Vault
Learn how to create secrets in Azure Key Vault and easily access them in a Micronaut application.
Authors: Sergio del Amo, John Shingler, Slavko Bodvanski
Micronaut Version: 4.10.9
1. Getting Started
In this guide, we will create a Micronaut application written in Groovy.
2. What you will need
To complete this guide, you will need the following:
-
Some time on your hands
-
A decent text editor or IDE (e.g. IntelliJ IDEA)
-
JDK 21 or greater installed with
JAVA_HOMEconfigured appropriately
-
A paid or free trial Microsoft Azure account (create an account at Azure account signup)
3. Creating the Application
Download the complete solution of the Access a database with Micronaut Data JDBC guide. You will use the sample application as a starting point.
4. Micronaut Azure Key Vault Dependencies
Add the following dependency:
5. Update the Application configuration to use Azure Key Vault secrets
5.1. Add the Azure Key Vault secret placeholders to the Application Configuration
+ datasources.default.username: ${JDBC-USER}
+ datasources.default.password: ${JDBC-PASSWORD}| The Azure Key Vault secrets naming convention does not allow "_" to be used as a word joiner. Therefore, when adding JDBC secret placeholders, you should use "-" instead (e.g. JDBC-USER, JDBC-PASSWORD). |
5.2. Enable Distributed Configuration
Create a bootstrap.properties file in the resources directory to enable distributed configuration.
Add the following:
(1)
micronaut.application.name=micronautguide
(2)
micronaut.config-client.enabled=true| 1 | Set the application name in bootstrap.properties instead of application.properties so that it is available when reading configuration from distributed sources.
properties |
| 2 | Set micronaut.config-client.enabled=true which is used to read and resolve configuration from distributed sources. |
5.3. Clean up Application Configuration
If application.properties sets micronaut.application.name, remove it. You moved it to bootstrap.properties.
micronaut.application.name=micronautguide5.4. Disable Distributed Configuration for Test
You can disable distributed configuration in a test by annotating a test with:
@Property(name = "micronaut.config-client.enabled", value = StringUtils.FALSE)
@MicronautTest5.5. Azure Bootstrap Configuration
Add the following configuration for Azure bootstrap.properties:
azure.credential.client-secret=
(1)
azure.credential.client-id=${AZURE_CLIENT_ID}
(2)
azure.credential.tenant-id=${AZURE_TENANT_ID}
(3)
azure.credential.secret=${AZURE_SECRET_VALUE}
(4)
azure.key-vault.vault-url=${AZURE_VAULT_URI}| 1 | The client ID of the trusted application that you will register in Azure Portal |
| 2 | The tenant ID |
| 3 | The secret value of the registered application |
| 4 | The Azure Key Vault resource URI |
| More details on how to obtain these values are provided in the Azure Portal section below. |
5.6. Clean up the Application Configuration
Remove the redundant application name entry from the application.properties.
- micronaut.application.name=micronautguide6. Store JDBC secrets in Azure Key Vault using Azure Portal
Create Azure Key Vault service resource.
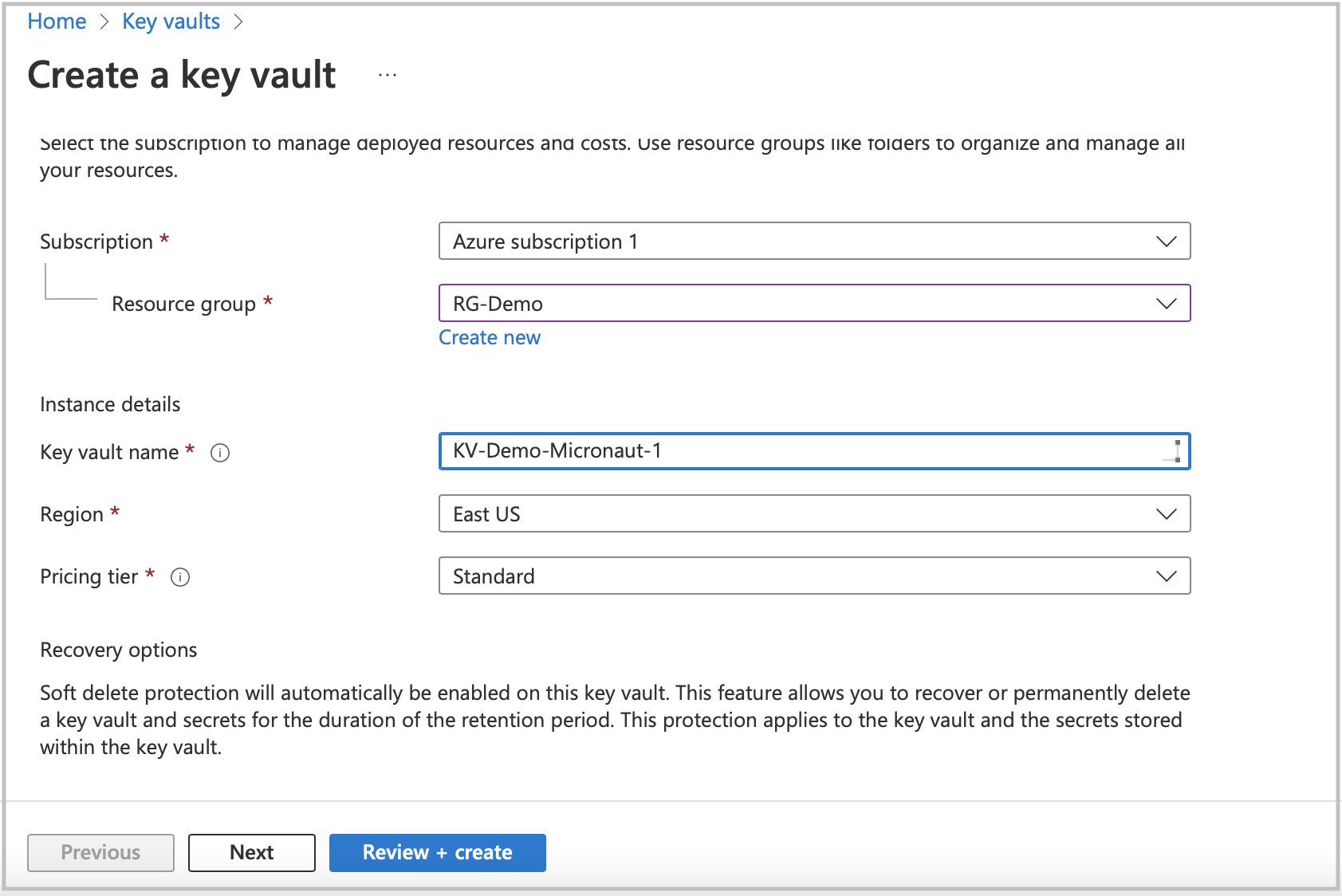
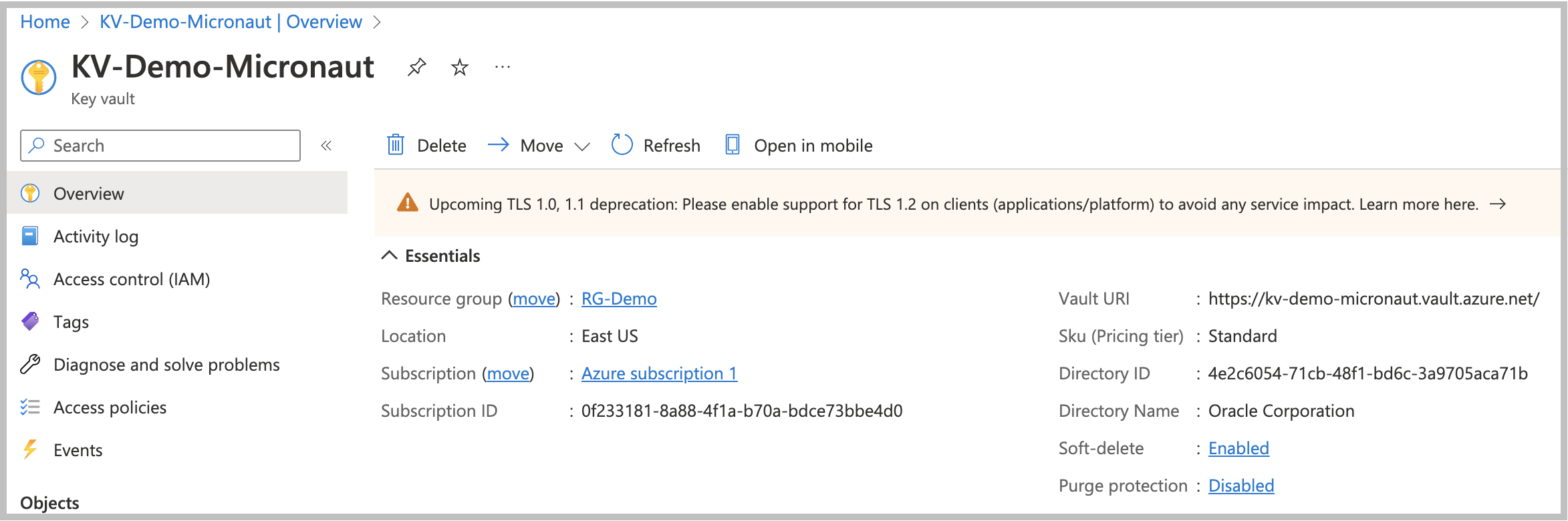
When Key Vault service deployment is ready, go to the resource to create secrets. Before clicking on the Secrets option in the left menu list, copy the Vault URI from the main screen section. You will need to set it as an environment variable to integrate Azure Key Vault into your application.
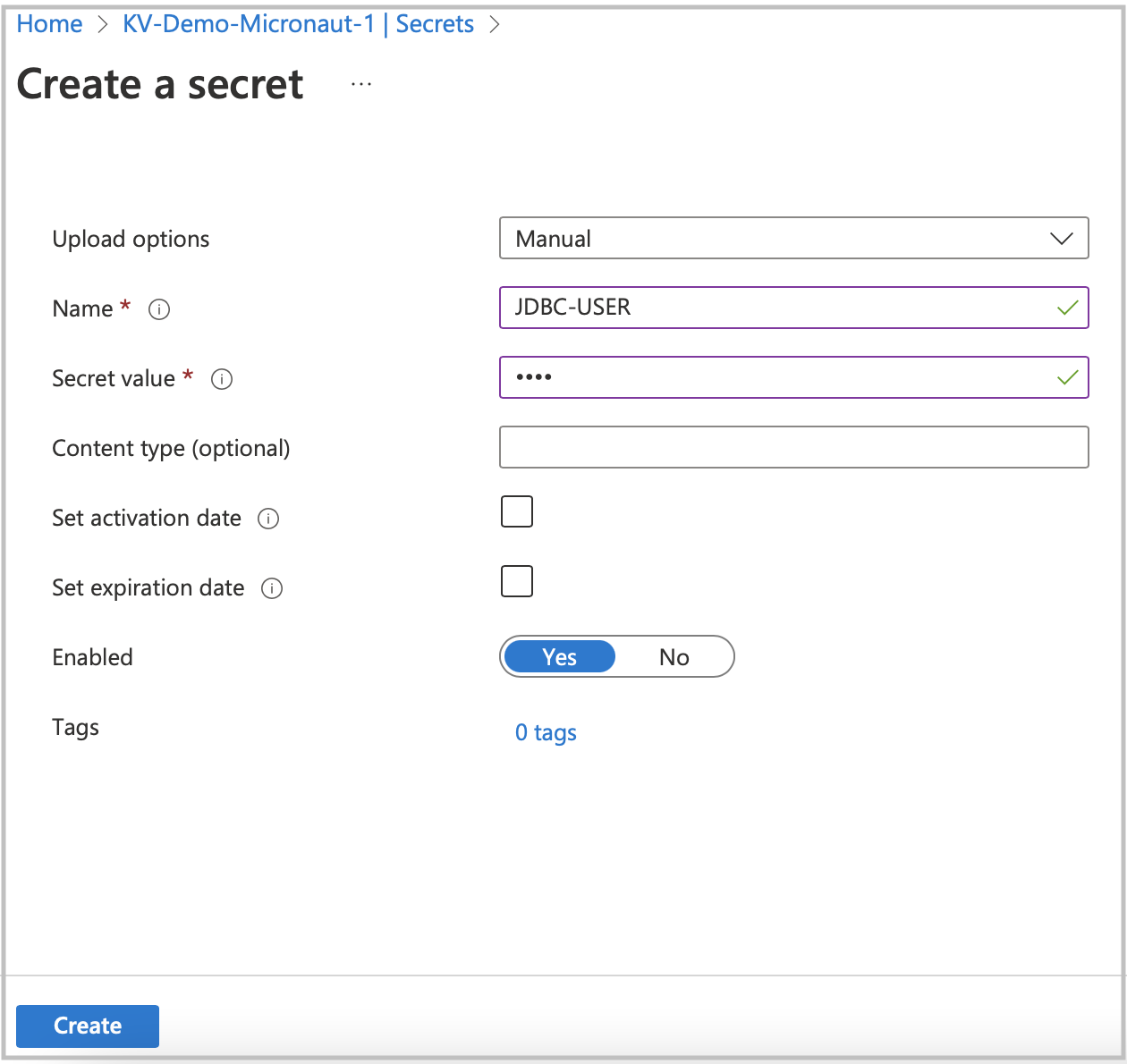
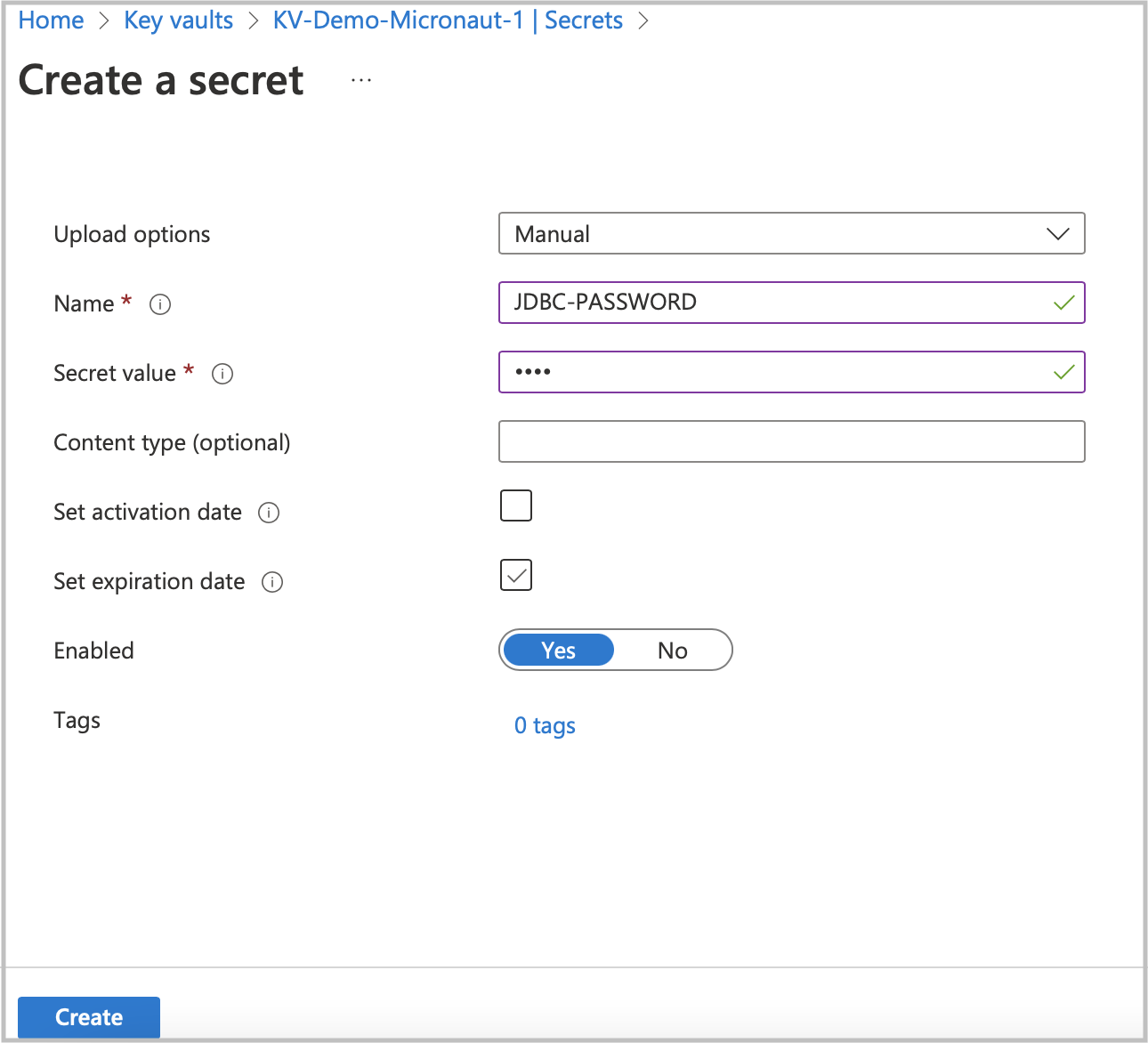
Create new secrets for JDBC user and password. Click on the Secrets option in the left menu, then click on Generate/Import.
Go to App registration to register your application with the Microsoft identity platform. After registering your application,
copy the secret Application (client) ID, and Directory (tenant) ID. You will use them later as environment variables to connect to Azure Key Vault.
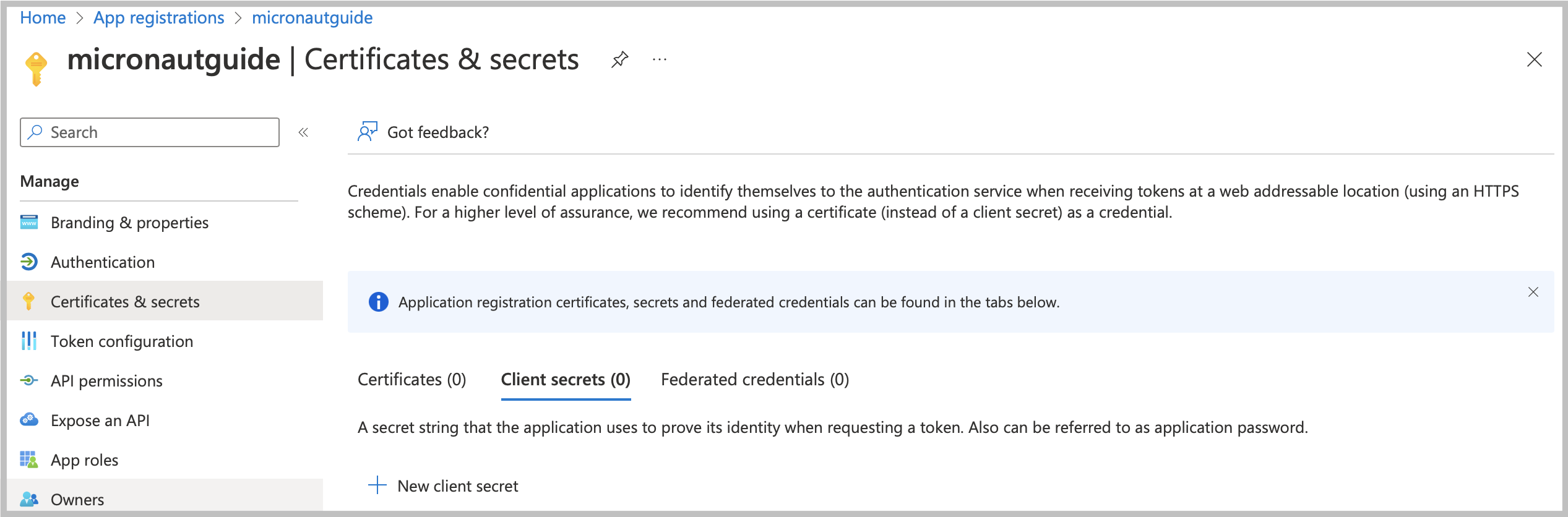
Navigate to your application profile to generate application credentials that you will use to authenticate with the Azure Key Vault service. In the left menu, click on the Certificates & secrets. To generate the application credentials, click on the Client secrets tab and then on the New client secret button. Copy the secret value. You must set it along the Application (client) ID, Directory (tenant) ID, and Vault URI as environment variables.
|
The client’s secret value cannot be viewed, except immediately after creation. Be sure to save the secret when created before leaving the page
|
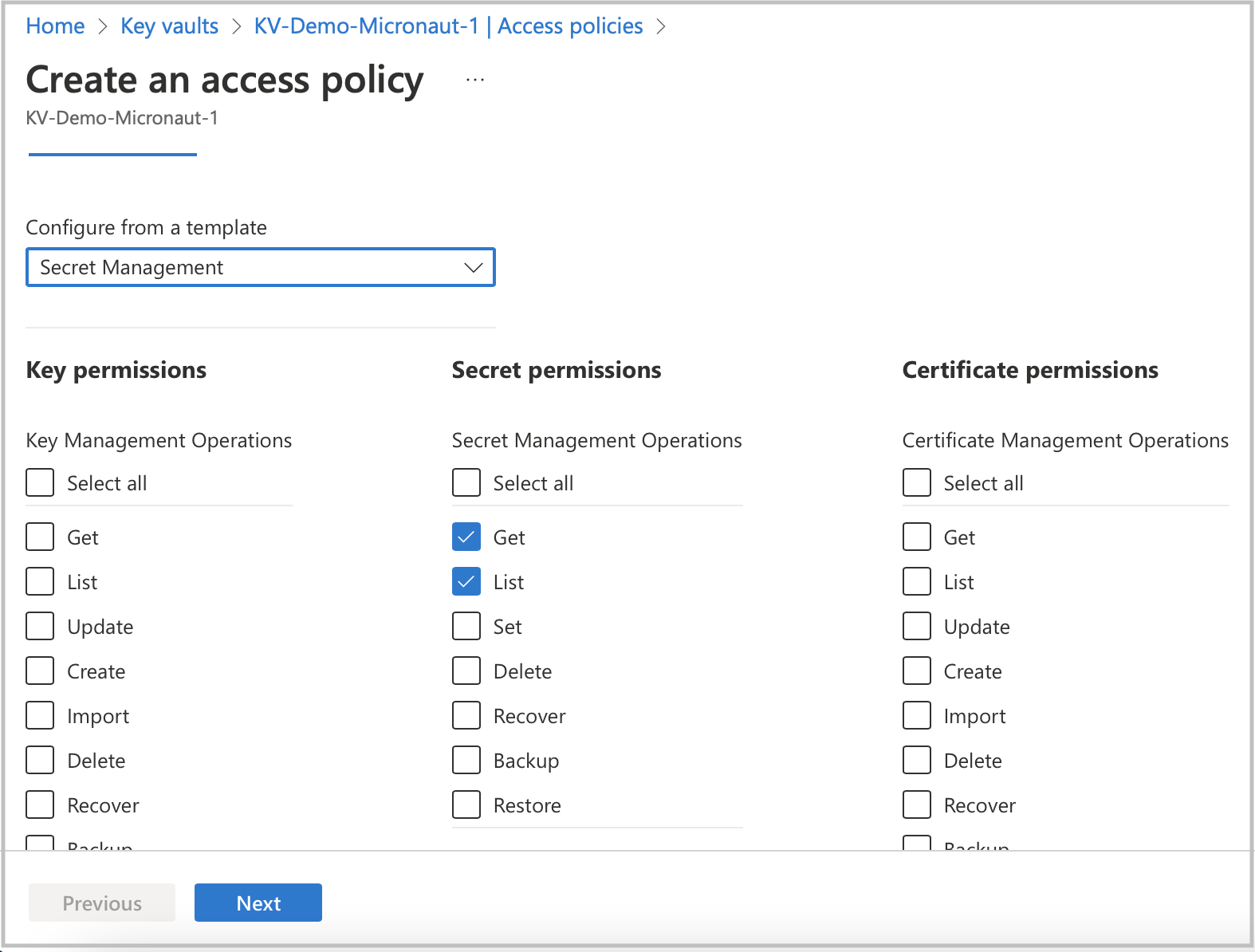
To finish the Key Vault setup process. You will need to assign a proper policy to the Key Vault resource.
-
Go to your Key Vault resource profile.
-
Click on the Access policies option in the left menu.
-
Select Get and List options from the Secret Management Operations list.
-
Finally, create an access policy.
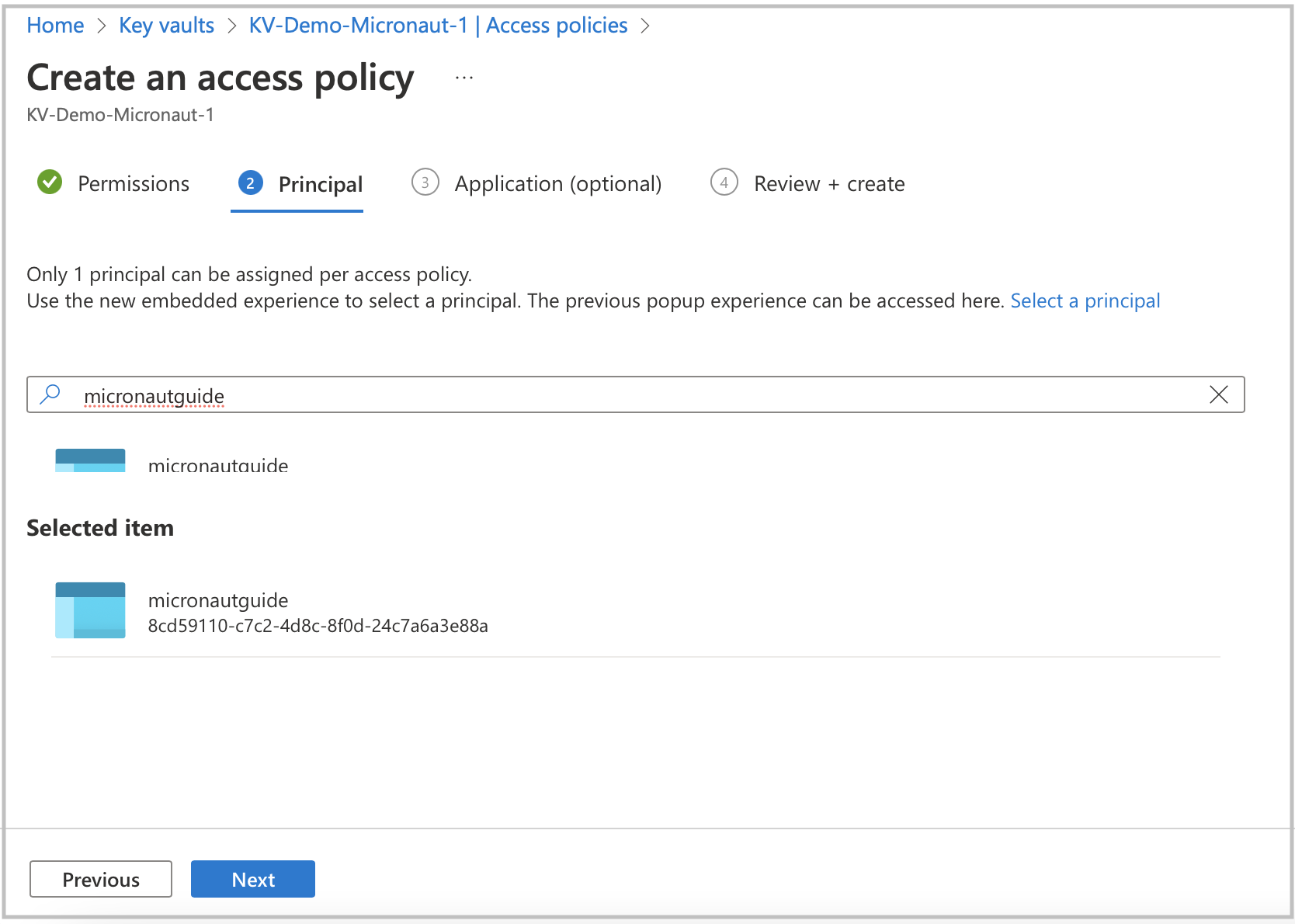
Prior to completing the policy creation process, a security principal should be assigned. The policy should refer to your application acting as a security principal.
7. Running the Application
With almost everything in place, you can start the application and try it out. First, set environment variables to configure the application datasource, then start the application.
Create environment variables for AZURE_CLIENT_ID, AZURE_TENANT_ID, AZURE_SECRET_VALUE, and AZURE_VAULT_URI, which will be used in the Micronaut app’s application.properties datasource:
export AZURE_CLIENT_ID=<the client id from the Azure configuration step>
export AZURE_TENANT_ID=<the tenant id from the Azure configuration step>
export AZURE_SECRET_VALUE=<the secret value from the Azure configuration step>
export AZURE_VAULT_URI=<the vault URI from the Azure configuration step>To run the application, use the ./mvnw mn:run command, which starts the application on port 8080.
You can test the application in a web browser or with cURL.
Run from a terminal window to create a Genre:
curl -X "POST" "http://localhost:8080/genres" \
-H 'Content-Type: application/json; charset=utf-8' \
-d $'{ "name": "music" }'and run this to list the genres:
curl http://localhost:8080/genres/list8. Cleaning Up
After you have finished this guide, you can clean up the resources you created on Azure Cloud so you won’t be billed for them in the future.
9. Next Steps
Explore more features with Micronaut Guides.
Read more about:
10. Help with the Micronaut Framework
The Micronaut Foundation sponsored the creation of this Guide. A variety of consulting and support services are available.
11. License
| All guides are released with an Apache license 2.0 license for the code and a Creative Commons Attribution 4.0 license for the writing and media (images…). |